100% Pass Cisco, PMP, CISA, CISM, AWS Dumps on SALE!
Get Now
01:59:56
X
How does the Internet interconnect various networks?
Of course, the home network, enterprise network, and data center are connected to the operator's access network through optical fiber. The trickle flows from the access network are aggregated into super-large traffic, which is transmitted to the core switching network using higher-speed optical fiber links, where it is distributed to all corners of the world according to the destination of the traffic.
The popular science articles that we often see on the Internet, the pictures that see the Internet usually look like this:

After reading these pictures, I still can't understand how the Internet is connected. To understand the local connection information, you can refer to this picture:
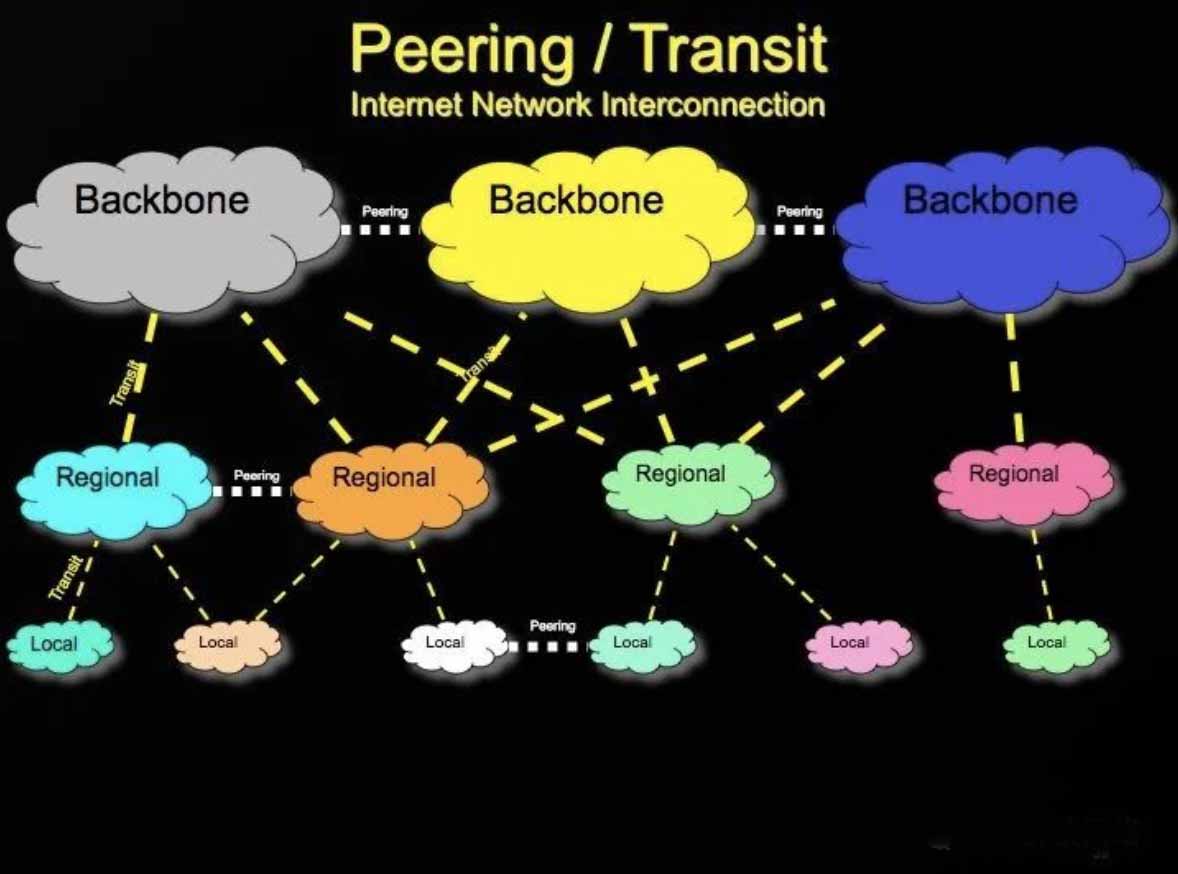
Each Backbone in the picture can represent an operator. You can think of them as "China Telecom", "China Unicom", and "China Mobile". Each operator, like an independent kingdom, uses an AS number to exchange global routing tables with other kingdoms.
In this picture, a three-layer traffic architecture model is also used: Local, Regional, and Backbone. For communication between different operators, if there is interconnection at the access layer, directly go through the access layer link to complete the exchange. The link marked "Peering" in the figure.
If the access layer is not interconnected, the traffic will go upstream to the aggregation layer. If the aggregation layer has interconnection, go directly to the aggregation layer link to complete the exchange.
If there is neither, the traffic will eventually go up to the core network, where to complete the exchange, then down to the convergence layer, and finally to the access layer. Not to mention a lot of injustice, traffic between operators is easily stuck on the interconnection link. Because all cross-operator traffic must go through this narrow one-way bridge, it is common to roll over and fall into the water.
No matter if you have hardware (interface/optical fiber) or software, you need to grasp both hands, hard and soft.
What about software?
BGP is essential as software. BGP is mainly used to exchange global routing tables with other operators. In order to uniquely identify each operator, each company has its own unique AS number.
Operators can directly establish BGP neighbor relationship (Peering), with or without interoperability, and bidirectional synchronization of global routing tables. With the global routing table, traffic can follow the navigation instructions of the routing table and run away. . .
Sometimes operators will exchange routing tables indirectly. What does indirect mean?
The so-called indirect means that there is an Internet server, each operator establishes a BGP neighbor relationship with it, and uploads its own routing table to it. Then it distributes (downloads) the collected global routing table to each operator.
Operators are first and foremost a cooperative relationship. Without mutual cooperation, there is no Internet at all. In the spirit of "Everyone is for me, I am for everyone", we have the Internet all over the world today. However, operators are also in a competitive relationship, and the Internet cake will not grow indefinitely. Of course, competition is not a bad thing, competition will have quality service. There is also traffic settlement between operators, and inbound and outbound traffic settlement.
The Internet is extremely complicated, so it is impossible to explain the problem with a picture. A medium and large-scale network that was once managed has 6700+ multiple switches/routers/firewalls and 30000+ servers worldwide. Distributed in more than 100 countries, more than 700 Sites. Connect these devices through LAN links, WAN links, and then connect to the Internet through Internet links. There are more than 300 optical Internet links. This is just an enterprise network. In addition to the home network, there are tens of millions of companies in the world. If you use a topological picture, it is ten million times more complicated than the spider web.
This is why a complete network topology map can never be found in the company. Complexity is on the one hand and security on the other. The complete network topology is obtained by the bad guys, and the destructive power cannot be estimated.
The above is the news sharing from the PASSHOT. I hope it can be inspired you. If you think today' s content is not too bad, you are welcome to share it with other friends. There are more latest Linux dumps, CCNA 200-301 dumps, CCNP Written dumps and CCIE Written dumps waiting for you.
Cisco Dumps Popular Search:
what is the new ccna ccna 200 301 changes ccie hall of fame ccie rs lab v6 ccnp tshoot gns3 tickets ccnp switch 300-115 study notes ccnp 300-435 ccnp switch 300-115 labsim cisco sample exam ccna 200-301 todd lammle
Copyright © 2025 PASSHOT All rights reserved.






