100% Pass Cisco, PMP, CISA, CISM, AWS Dumps on SALE!
Get Now
01:59:56
X
What is Access Token?
How to ensure that the authentication information (AccessToken, etc.) sent by the client is not obtained or forged? Which encryption method would be better?
What is Access Token?
Websites with user name / password login, even websites that use mobile phone numbers / SMS verification codes, including Zhihu and WeChat public accounts, after Alice completes a successful user authentication, she will be pushed to Alice with an "Access Token", as shown below The highlighted part of the link is shown.
http://example.com/home.jsp?
UID = 7B216A634951170FF851D6CC68FC9537858795A28ED4AA6F
Alice visits the website later, as long as the Access Token is embedded in the URL access request, the server will know that Alice is visiting the website. In short, Access Token is a substitute for Username / Password.
If this UID is captured by Evil, as long as Evil copies the URL link into the address bar and presses Enter, the server does not know whether the opposite is Evil or Alice, but because the Access Token is Alice, the server thinks that it is visiting the website Is Alice.
The use of plaintext http transmission is inevitable for third parties to peep and intercept Alice's Access Token. Therefore, for the security of Access Token, encryption at the transport layer is required. Only SSL / TLS encryption is required, and Evil has no way to peep and intercept the UID.
https://example.com/home.jsp?
UID = 7B216A634951170FF851D6CC68FC9537858795A28ED4AA6F
This link starts with https, which means that the link is encrypted at the transport layer. This is not the case in the process of encrypted transmission, it is a bunch of seemingly messy byte streams.
When the encrypted byte stream reaches the server, the server encrypts the URL shown in plain text as shown above, extracts the UID, and recognizes it as Alice.
On this earth, except for Alice who has a chance to see the long string of UID = 7B216A634951170FF851D6CC68FC9537858795A28ED4AA6F, the only thing left is the server, which is the original goal of transport layer encryption. Transport layer encryption is end-to-end encryption, and only the communicating parties can decrypt the encrypted content.
However, many websites will use third-party web pages to accelerate services, and third-party service providers can decrypt this string, so you can see that there is one more member in this string. In a sense, this is a legitimate member. .
Also, the PASSHOT article tirelessly says that SSL / TLS is at risk of being spoofed by forged certificates. If the client reminds Alice that the certificate is insecure and Alice still chooses to trust the certificate, this fourth party who tries certificate spoofing can also see So far, so far, the number of members has increased to four, and this is an illegal member (fourth party).
There was a problem in the PASSHOT learning group that was discussed very hotly. The user password is encrypted in the background of the server. What is the significance of the client encrypted password?
No matter how the password is handled, the user accesses the website by Access Token. The fourth party members above can use the Access Token to impersonate Alice's identity. As for Alice's password, Who Care!
Therefore, to prevent Access Token from leaking, the most important measure is to ensure the security of https encrypted communication. Once the client finds that the server certificate verification is illegal, it directly exits instead of letting the user choose whether to continue.
Alice ’s long string is an ID. The server uses the ID as an index to query the database and pull out the user name, user group, and user permissions? Or does the string itself contain the user name, user group, and user rights, but it is only encrypted by the server. After the server receives it, it decrypts it with a key known only by the server to obtain the user name, user group, and user rights?
The former is Access ID, the latter is Access Token!
Since the Access Token itself contains user permission information, the server does not need to maintain the user's state. Every time the Token is decrypted, the user's permission information can be obtained in real time. The server only needs to remember the decryption key.
Does Access Token use asymmetric RSA encryption or symmetric encryption?
RSA encryption / decryption has a high calculation time cost and is generally used for one-time authentication. And every time the user refreshes the page, they need to verify the token once, which is not suitable for RSA verification. Therefore, the algorithm for encrypting Access Token generally chooses symmetric encryption, such as AES CBC and DES encryption.
Alice stared at her long Token for a long time. If you modify the string and the user name decrypted by the server is "Admin", can't Alice impersonate the server's administrator? With this permission, you can do whatever you want! Alice found the "Padding Oracle" script on the Internet. Every time Alice modified one bit (blackened number) of the initialization vector (IV), and then sent it to the server, the server would pop up a message box. This message box said: The server decrypted There is a Padding error.
Request: http: //sampleapp/home.jsp? UID = 0000000000000001F851D6CC68FC9537
Response: 500-Internal Server Error
Then Alice continued to modify the IV and sent it to the server again and again. The server finally bounced back a message:
Request: http: //sampleapp/home.jsp? UID = 000000000000003CF851D6CC68FC9537
Response: 200 OK
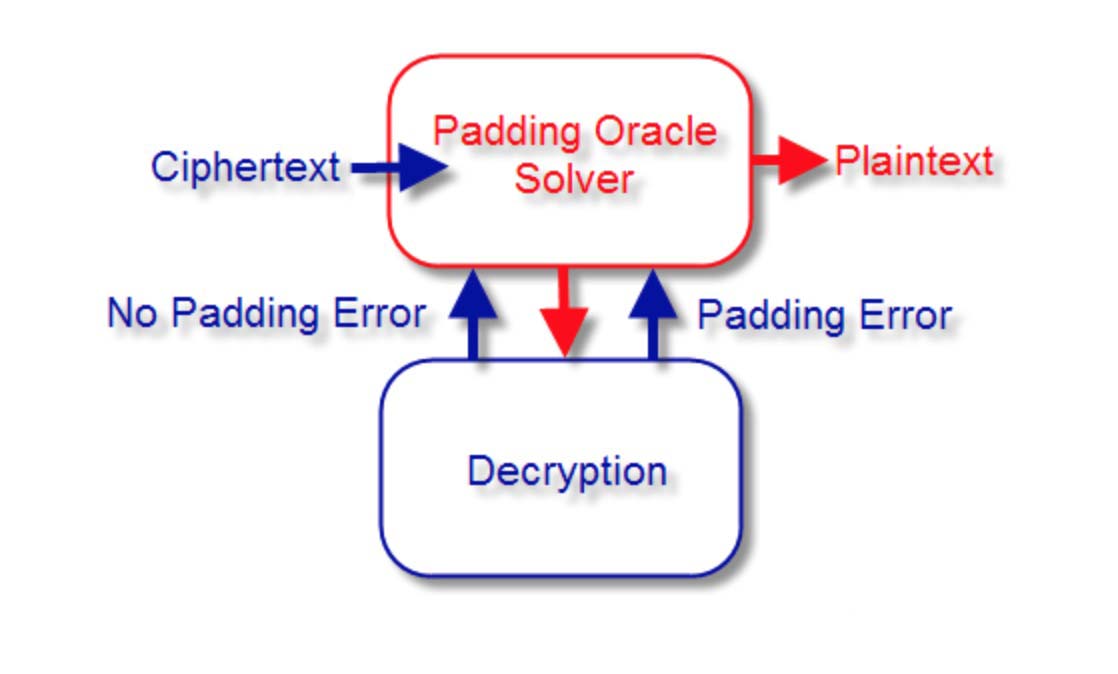
The meaning of this message is that Padding verification is successful. For a byte, Alice can try to crack at most 256 times. Then continue to iterate in this way, a 16-byte Token, in theory, only need to send 16 * 256 = 4096 times to completely decrypt the plaintext content of the Token.
Padding Oracle
What is used is that each attempt of the server to the client is reported with a right or wrong prompt to facilitate the attack. There is a guessing game like this: the host said on stage, I have a secret, anyone can ask me questions, I will answer right or wrong, whoever guesses my secret first, who is the last winner!
If the host modifies the rules of the game, when someone asks whether it is right or not, they will say nothing, and it will be much more difficult for others to guess the answer, and they will never even be able to guess!
This attack method made websites that use AES CBC encrypted Tokens like enemy a few years ago, and modified message boxes one after another. If the decryption of the user Token, whether it is Padding verification success or failure, it is the same reply. Failure.
In addition, encryption algorithms that do not use Padding, such as RC4 and AES GCM modes, can also be used to deal with Padding Oracle attacks.
The above is the news sharing from the PASSHOT. I hope it can be inspired you. If you think today' s content is not too bad, you are welcome to share it with other friends. There are more latest Linux dumps, CCNA 200-301 dumps and CCNP Written dumps waiting for you.
Cisco Dumps Popular Search:
ccie rs 400 101 written dumps certcollection cisco courses ccna ccnp encor 350-401 training ccnp route objectives ccna 4 chapter 4 ccna questions and answers pdf ccnp switch pass mark spoto ccie security lab zip rar ccna routing and switching pdf download 9tut ccnp switch 300-115 pdf
Copyright © 2025 PASSHOT All rights reserved.






